Looking for Expert Advice?
We're here happy to help
With ransomware incidents reported daily, and consequences becoming more costly, maintaining a healthy respect for potentially dangerous attacks on your organization's data and information systems seems prudent, if not critical.
The universe of security technologies keeps growing, and that's a good thing. As new threats emerge, new solutions are created to counteract them. But this phenomenon seems to only demand more expertise, more decisions, and more investment from organizations trying to protect themselves, and it will likely only get worse.
You might be tempted to believe disaster is imminent if you buy into the level of sophistication attributed to hackers by the mass media. But while a cyber attack can bring an organization to its knees, most exploits are, frankly, not very sophisticated.
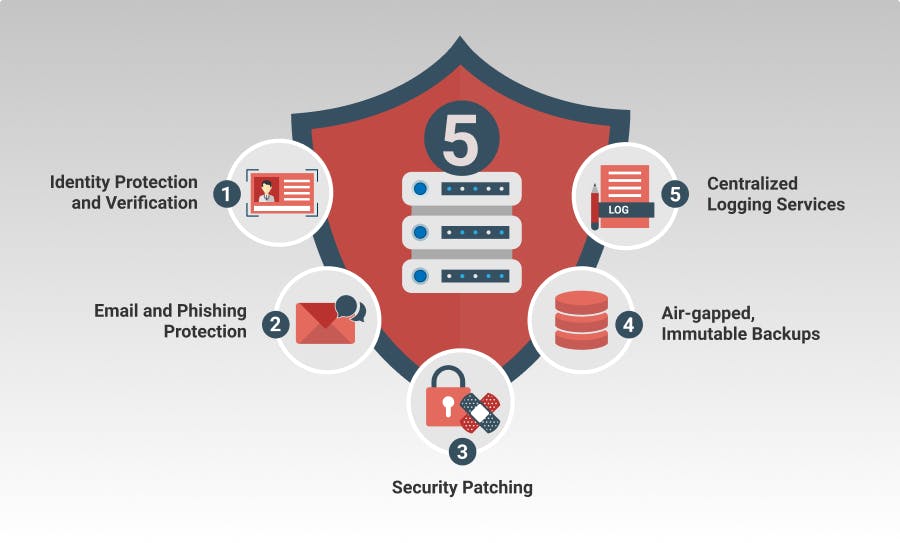
Truth is, while securing your IT infrastructure isn't necessarily easy, you'll be well-positioned to weather most attacks if you focus on no more than the essentials, or the points outlined below comprising what we refer to as Baseline 5 Cybersecurity. This article outlines the five relatively simple, low-cost and minimally intrusive measures IT leaders can and should implement—often with the software and tools already at their disposal—that will put their organizations among the leaders of the pack when it comes to cybersecurity readiness, and leave them far less likely to have to deal with the effects of a successful breach.
Baseline 5 Cybersecurity starts with the assumption that your organization already has a firewall and an end point protection solution and that those solutions are relatively modern.

In organizations without a single sign-on (SSO) solution, users are forced to remember different usernames, passwords, PINs and secret questions across up to dozens or more services and applications. Users inevitably encounter a variety of requirements pertaining to password length, complexity and longevity. Since users can't possibly keep track of them in their head, they learn to "cheat" by saving passwords on their phones, in a file or on a sticky note. They may use a small number of passwords—and similar variations thereof—across a range of applications and services in an effort to "manage the mess".
SSO eliminates the hassle of remembering scores of passwords. It not only makes users' lives easier (and their working hours more productive), it also reduces the likelihood of users maintaining insecure lists of account credentials.
Ironically, along with SSO comes a related risk: The possibility of a single compromised password granting access to a whole range of applications and data. Safeguarding the users' SSO credentials, then, is all the more important. This is where MFA comes in.
Multi-factor authentication, or MFA, dramatically improves an organization's security posture with limited day-to-day impact to users. In short, whereas SSO helps protect identity by making it more manageable, MFA helps services and applications verify an identity by asking the question "How do I know you are who you say you are?". Today's users are accustomed to MFA because it’s used by their bank, by their credit card companies, and even their social media platforms.

When it comes to cybersecurity, human behavior is the weakest link, the soft underbelly that is most often the target of the aspiring hacker's latest scam. The most common vector through which hackers exploit human behavior is ordinary email. It is the most used application by both organizations and cybercriminals, enabling malware delivery, phishing, impersonation attacks, and the spread of cyber threats that are already internal to your organization.
Modern email security solutions such as Mimecast can, in parallel with user training, minimize how often phishing scams are able to penetrate an organization and exploit email users. Such solutions are reliable, cost effective and in some cases provide both protection and training. As users are going about their business, they are quizzed when opening links: Do you think this link is safe? It’s a good way to reinforce awareness, while reporting indicates which users might need more training.

There are plenty of reasons organizations should be updating software, from compliance to feature improvements, but improved security ranks at the top. In practice, applying security patches regularly can seem daunting, and in fact requires a good deal of work up front to make the process manageable. This might include inventorying software and devices, standardizing on systems and configurations, and developing patch management processes that your team can capably execute.
Patching, done properly and thoroughly, is challenging. Different vendors and products often require different approaches and processes. Given the potential complexity of an effective patching program, organizations commonly delegate this activity to a managed IT services provider, who is likely to be equipped with tools to help automate these processes.

As with the first three measures above, the focus of cybersecurity Inside many organizations has long been on incident prevention, or trying to keep the bad guys out. What we have witnessed over the last several years is that regardless of how much organizations invest in winning the war against cyber crime through prevention, there is always the likelihood that bad guys are going to occasionally win a battle, resulting in another victim of a ransomware attack. An important part of your cybersecurity plan, then, covers what you will do when you are breached.
Your ability to recover from a disaster starts with having air-gapped, immutable backups. Air-gapped means that backup copies cannot be reached electronically. Immutable means that—breached or not—your backup copies cannot be changed. These two measures ensure that bad guys can neither touch your backups nor change, or encrypt, backup data to demand a ransom. Some backup solutions are better than others—particularly in modern, hybrid environments—but the good news is that most solutions on the market can be configured to provide this type of protection.

If all of the preventative measures taken by an organization fail to prevent a serious cyber incident, regardless of how successful its recovery, the ability to determine with certainty what went wrong is crucial to avoiding a repeat incident. A Security Information and Event Management (SIEM) solution aggregates, indexes and correlates the activity reported by all of an organization's services, devices and systems. It can, in some situations, even detect suspicious activity and alert stakeholders before the activity turns into a real problem, meaning that SIEM spans both preventative and forensic aspects of security. SIEM solutions are critical when it comes to figuring out, after a breach, what happened: How did the bad guys get in? Where did they go? What did they take? Failing to address a vulnerability after an incident is an open invitation to cyber criminals to attack again.
Attaining Baseline 5 Cybersecurity should not be an organization's only security goal. Specific use cases often demand specific additional security measures. Based on our experience, though, most organizations are not Baseline 5 compliant, and these shortcomings are more likely than others to lead to a cyber incident.
Prescriptive Data Solutions is here to help. Contact us today to discuss a Baseline 5 Security Audit for your organization.