
Minding the Security Gap
Protecting an organization’s data and assets from the inherent vulnerabilities posed by the very the technologies on which we’ve grown so dependent has become the business challenge of the ages. But if I didn’t traffic in cybersecurity solutions on a daily basis, and if I were still witness to the actions—or maybe I should say inaction—on the part of executives who haven’t yet felt—or at least witnessed from a distance—the pain of a serious data breach or crippling ransomware attack, I might draw the conclusion that things aren’t so bad out there.
I know better. Threats have only worsened, both in quantity and severity. So it begs the question: If the danger is so great, why does it most always take another news story recounting the collapse of some company’s stock as a result of a cybersecurity failure to inspire onlookers to take cybersecurity seriously, to take concrete steps toward avoiding a crisis of their own?
I have a theory. You’ve heard of the principle of breaking a problem down into smaller chunks to make solving it more manageable, right? Our brains are better at solving problems when the problems are simpler. It doesn’t mean we can’t solve complex problems. It just means that we solve them better when we manage to tear them apart, so to speak, and address them in smaller pieces. Failure to do this makes problems harder to solve than they need to be. And, getting to my point, it also makes the problem a whole lot easier to set aside until tomorrow. Tomorrow has a way of never arriving. Until one day, it does, and nobody likes that day.
But what does this have to do with cybersecurity? It’s a complex problem, you say, so let’s just break it down into simpler problems. And yes, I’m on board with that! But my theory is that the topic, the pursuit, of cybersecurity can be so vast and overwhelming—and you might even throw in slippery as a descriptor—that breaking it down isn’t necessarily an intuitive process.
Consider this, a high-level map of what I’ll label “cybersecurity domains”:
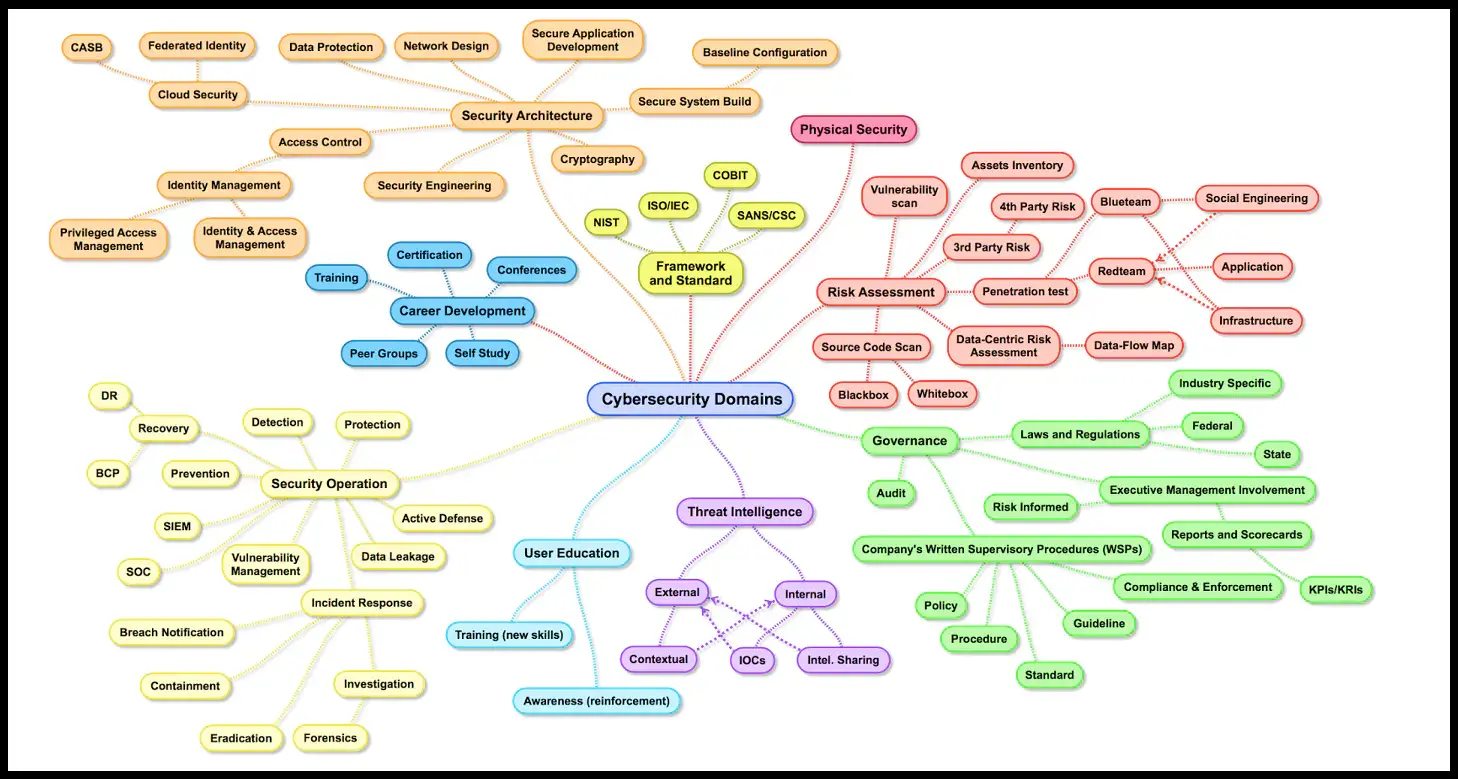
Pretty colors, if you’re into pastels. Lots of little bubbles, one might proclaim. An academic masterpiece, says me. But, as descriptive and detailed as this diagram may be, do you think it’s going to help “simplify” a problem? More like salt on a wound, rather. I’m not suggesting there’s no value in a good comprehensive diagram. I’m simply restating the obvious, which is that complex diagrams don’t always illuminate the best path forward.
It just so happens that NIST, the National Institute of Standards and Technology, promotes use of a Cybersecurity Framework, which, at it’s highest level, is a bit more digestible:
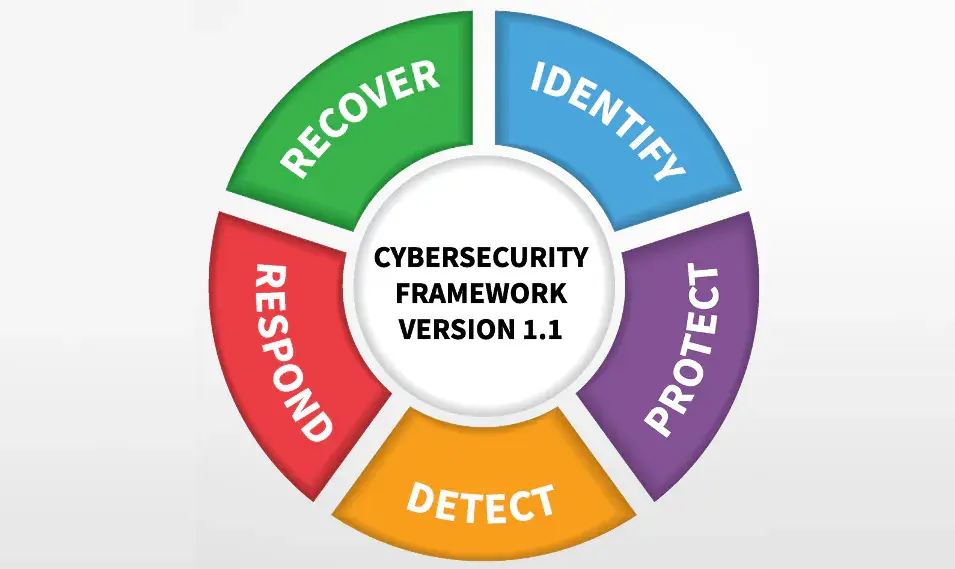
Beyond its simplicity, I also like that the Framework is action oriented. It gets right to the business of describing the activities which lead to desired outcomes, and, in case you were wondering, this framework goes much deeper into each one of the five steps (starting with “Identify”) listed. This is, indeed an excellent resource for CISOs and IT personnel tasked with leading cybersecurity initiatives. In the language of the Framework’s documentation:
The Framework is designed to complement existing business and cybersecurity operations. It can serve as the foundation for a new cybersecurity program or a mechanism for improving an existing program. The Framework provides a means of expressing cybersecurity requirements to business partners and customers and can help identify gaps in an organization’s cybersecurity practices.
A decidedly “top-down” approach, the Framework “core”, represented by the diagram above, is a good tool for initiating high-level discussions about security, which may be an ideal place to start when organizations are assessing their overall cybersecurity posture, attempting to get their arms around what’s at stake, and possibly identifying some areas where priorities lay.
Here, too, though, organizations can easily get bogged down. The framework is decidedly generic, completely technology agnostic, and avoids prescribing a step-by-step how-to process out of necessity. It’s a framework, in other words, not an instruction manual. Every organization is unique, each with a unique combination of needs and resources, so it’s no surprise that a framework would fall short of illuminating the path.
High-level conversations have a way of fizzling out. The Framework, developed in part to help identify cybersecurity gaps, will, without knowledge of how to transition downward from the 50,000-feet-level, invariably leads to a dead end. Asking the question “What are you not doing?” quickly becomes useless with no further plan for digging deeper.
This is where the introduction of “bottom-up” prompts breathe real life into a cybersecurity effort. At Prescriptive we value high-level conversations for helping getting a quick lay of the land. We can quickly get a sense of business priorities and broad technologies by talking to the right people. And people, I might add, are key to this whole process. But quickly shifting to bottom-up questions—getting down into the weeds of every day use cases—is where we really begin developing momentum in identifying security gaps. It’s filling these gaps, after all, that we’re after.
Here’s a glimpse of what an exchange arising from a bottom-up prompt might look like:
Sam (security consultant): How do your users get their email?
Barb (IT director): Oh, we use Microsoft 365.
Sam: Describe that process for me. Let’s take a user here in the office.
Barb: Well, normally we use the browser for just about everything around here, email included. So a user just pulls up the browser and logs in directly to the Microsoft 365 website.
Sam: How does the user get to that website, though? How does he get on the network, first of all?
Barb: Oh we’ve got several access points set up. Users all have laptops, and they can get on wifi from anywhere on the campus here.
Sam: So I can get on wifi?
Barb: Well, sure, if you know the key.
Sam: Okay, let’s put a pin in that can come back to it later. Okay, let’s assume they’re on the network, how does their browser request get routed?
Barb: We have a DNS server on prem, if that’s what you mean.
Sam: So your DNS server routes the user’s request to Microsoft?
Barb: Well, sort of. It forwards requests that it has no knowledge of to Google.
Sam: Ah, gotcha. Okay, let’s put a pin in that and come back to it.
This conversation can go on for some time, and it’s not atypical that within minutes we’ve “pinned” five or six vulnerabilities. We repeat these conversations with stakeholders throughout the business. Through this type of effort we develop a thorough picture of business priorities and security gaps, and we augment this with detailed data collected from the network itself, which ensures that we don’t miss anything, that we have every conversation needed to re-construct the big picture, keeping business priorities front and center.
This is not an earth-shattering revelation, I’ll agree. But so often the simplest approach is also the most effective, and sometimes the hardest to see. Combining the top-down approach of high-level conversations inspired by a good framework and the bottom-up prompts exploring specific use cases is deceptively simple and remarkably effective.
Do you want to know more? Contact Prescriptive to learn how partnering with Prescriptive Data Solutions on cybersecurity can help prepare your organization for tomorrow’s challenges.


.png)
.png)