
Protecting your Organization from Ransomware with Bitdefender
Organizations of all types and sizes are under ever-increasing threat from ransomware. Many high-profile businesses like Garmin and government entities like the state of Alabama, have elected to pay these ransoms, creating the false impression that there is no defense against these types of malicious attacks.
We were recently contacted by an organization that had been hit with a new strain of Medusa Locker. This organization had invested in a security suite, but their solution did not detect, respond, or prevent the infection, allowing it to spread throughout the organization. While many organizations feel adequately protected, many security suites, including some of the most popular ones, do not effectively protect against these strains of ransomware.
Technical Deep Dive
Medusa Locker is a type of ransomware that was discovered in late 2019. Previously, it utilized a Windows UAC exploit to effectively bypass built-in Windows protection controls. As ransomware attacks increase and affect all industries, an effective security solution must be in place to prevent an outbreak. This is where Bitdefender’s Gravity Zone Ultra for Enterprise suite comes into play. According to Bitdefender labs, “Over 400,000 variants of ransomware are created daily and 99% of them are only seen a single time before they are modified.”. Below we will cover the 3 categories of a successful strategy to detect, respond, and prevent ransomware, which is the very foundational core of a SoC response.
Detection
During the customer engagement, we were able to retain a copy of a zero-day ransomware variant of Medusa Locker that had not been previously seen in the wild. Upon detonating the ransomware in a controlled virtual environment, we observed that Bitdefender's Endpoint Detection and Response (EDR) recorded all events as they were unfolding.
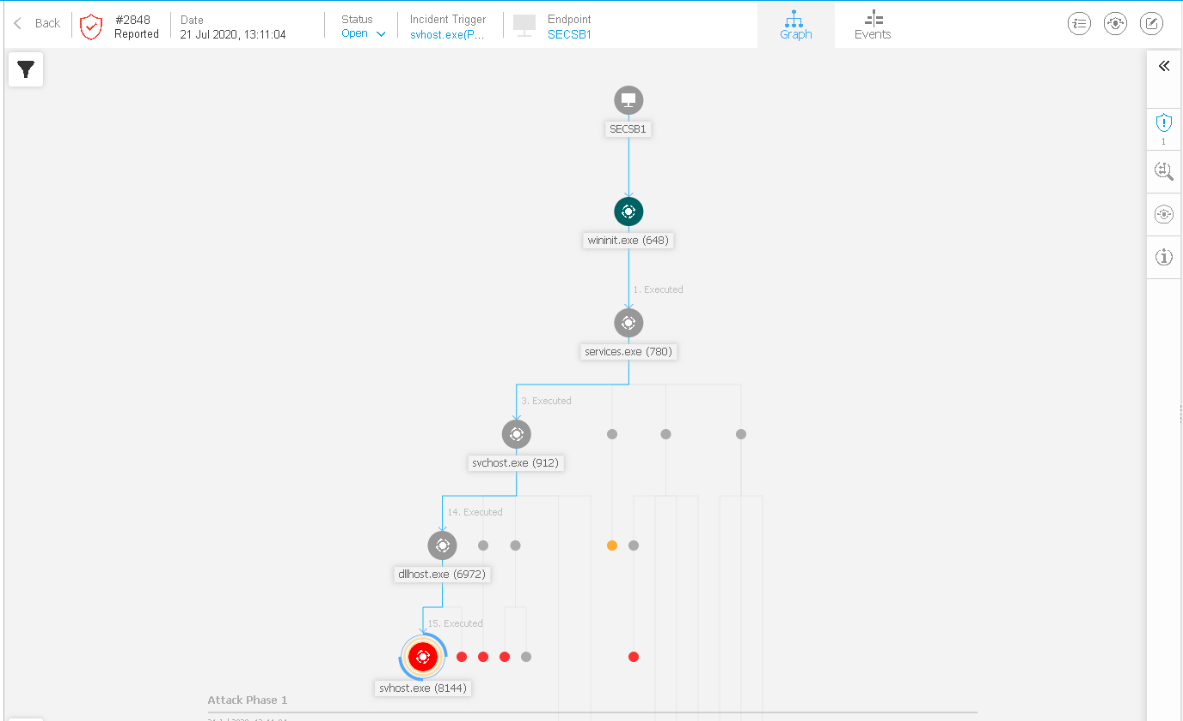
The endpoint protections in-depth logging of the event allowed us to track down all indicators of compromise that the ransomware variant had left behind. From within the EDR section of Gravity Zone, threat hunters can gather a transcript of the ransomware as it detonates. In our controlled lab environment, Bitdefender is deployed in an “Alert Only” state with the recommended configuration policy assigned to identify which layers of the protection suite would act against the threat. In a fully protected state, Bitdefender’s Advanced Threat control ( ATC) would have prevented the threat immediately while passing the malicious file through multiple reflective and machine learning models. This would have protected the organization immediately and prevented an escalated incident which would have required a disaster recovery engagement to resolve.
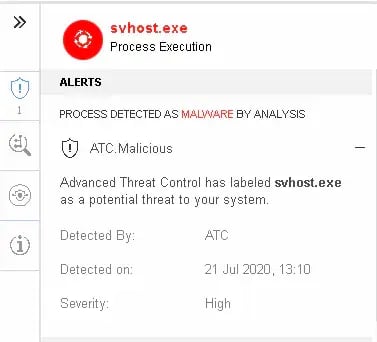
If the threat was missed by ATC, the patented “B-Have” heuristics engine would be utilized alongside of ATC as an additional layer of protection to identify it. This engine utilizes patterns of behaviors for known applications or threats and compares newly seen files to them to identify and detect if it is a threat.
As a third layer, the use of the built-in Anti-Exploit engine the organization can help protect applications from zero-day exploits in which ransomware may utilize to infect a system. Alerts may be generated and are shown in the main console and on the endpoint itself which can be an indicator of a malicious threat attempting to take advantage of a vulnerability in another legitimate program or the operating system as a part of its attack chain. During threat hunting this can be highly important to identify currently unknown threats in the environment.
Response
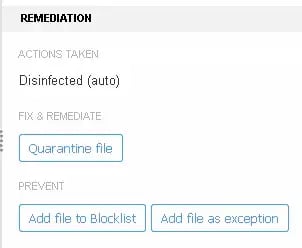
Bitdefender provides multiple response options for all forms of malware and network-based attacks. For ransomware you are able to kill, remediate, and quarantine the infection and its indicators of compromise on the host. If an endpoint detection and response incident is generated, you may also be able to remote shell into or isolate the system from the environment to help prevent the spread of the infection. Blacklisting can be done from within the incident screen as well, however blacklisting only covers the single executable and or file and not additional files that may have separate hashes.
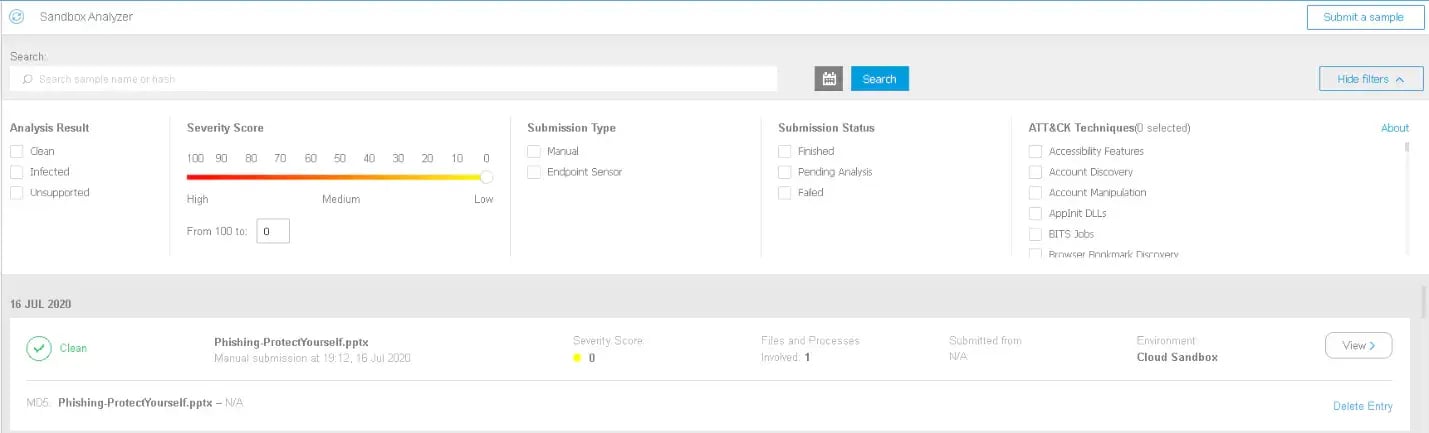
When configured in the endpoint protection policy, sandboxing of unknown scripts, documents, emails, and other items will automatically be performed and actions for threats that are investigated in the sandbox will be retroactively remediated on the endpoint after a conclusion is reached. You can view the results of sandboxing that has occurred in the Bitdefender Console under the “Sandbox Analyzer” tab.
While responding to a threat is key to remediating an issue that is currently in motion, it is always best to implement prevention measures before a threat occurs. In the next section of this article we will begin covering how to prevent Ransomware by utilizing Bitdefender’s product suite.
Prevention
In the response section of this article we discussed controls that can be enabled to prevent ransomware in an enterprise environment. We will now cover how we can harden the policies and controls to prevent the infection prior to it reaching the endpoint. These measures are extremely important as even fortune 500 companies suffer from insufficient risk, patch, and vulnerability management.
Bitdefender provides the following as part of a hardening approach against vulnerabilities and ransomware:
· Application Inventory and their current vulnerability state with CVE’s for remediation steps
· Patch Management as an additional addon which also patches 3rd party applications to help keep the environment current.
· Human Risk Analytics to review changes made to the endpoint by an individual user or list of users that may cause vulnerabilities or lead to malicious behavior
· Endpoint Risk Analytics to review current Microsoft and 3rd party product configuration issues on the endpoint with limited automated remediation
· Storage protection for NAS platforms
· Policy configuration hardening within the platform itself
Application Inventory
The Application Inventory can be seen under the “Network -> Patch Inventory” section of the console. From here you can see the patch name which will be utilized to remediate the vulnerability found out to the right under the Bulletin ID field.
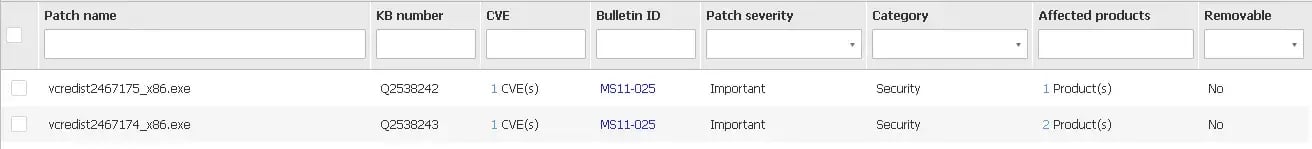
You can sort the vulnerabilities like an excel sheet, this will help you target specific applications and vulnerabilities within your network. You may also check mark and deploy specific vulnerability remediations right from the same screen.
Patch Management
Patch Management is another useful hardening tool to assist enterprises in keeping their systems up-to-date. This module is an add-on however it does not require a new Agent or installation after the endpoint security agent has been deployed. This can be extremely helpful when patching 3rd party systems that may not be able to be joined to the corporate domain for patch management by other tools such as SCCM. Patch Management schedules can be configured under Policies -> Policy Name -> Patch Management. If bandwidth is an issue you are able to deploy Patch Caching Servers into the enterprise at the location(s) that have lower bandwidth to store copies of the needed patches in a central location reducing the load on the network.
Endpoint & Human Risk Management
The Risk Analytics component is bundled underneath a single section labeled “Risk Management”, from there you are able to locate a high-level view of the company's: overall risk score, top human risks, top misconfigurations, top vulnerable apps, and endpoints / workstations by severity.
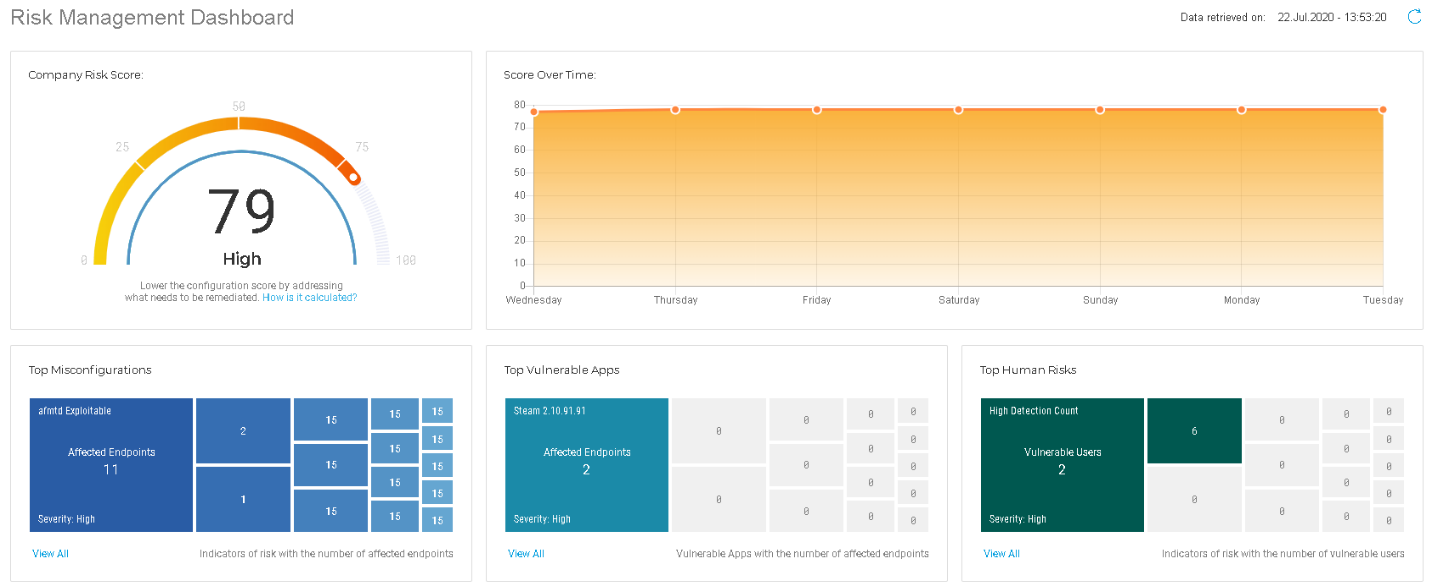
Drilling further there is a subsection of the Risk Management tab that is labeled “Security Risks”. From this section you are able see the risks broken down into categories: Misconfigurations, App Vulnerabilities, Human Risks, Devices, and Users. This helps you identify potential ransomware susceptible vulnerabilities, configurations, and exploits that the environment may be exposed to.

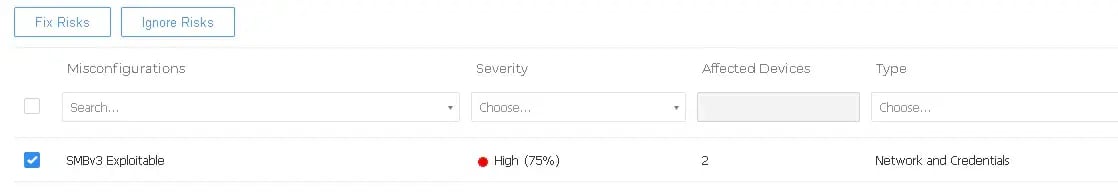
Under the Misconfigurations section you can check mark individual items and choose to issue a “Fix Risks” command from the console to initiate the endpoint protection to take the necessary steps to remediate the risk. In the example below in the “Misconfigurations” section you will see an SMBv3 exploit that can be automatically fixed which could be utilized as a ransomware attack vector to spread internally within a network.
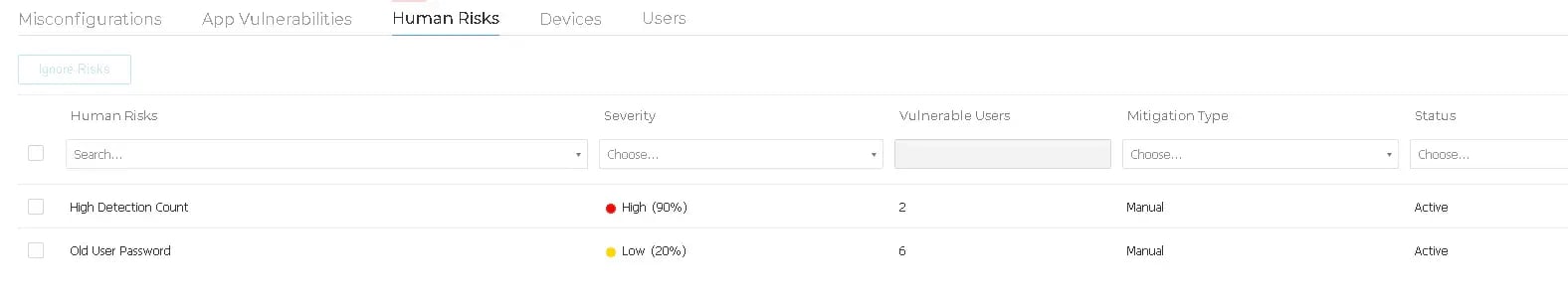
You can also sort these similar to the first Risk Management section and you are provided with a severity level associated with the risk listed. The Human Risks section will cover items like “High Device Counts”, “Old / unchanged User Passwords”, and more. By utilizing High Device Count as an example, if an administrator level account is located on multiple devices or a service account is present it can be utilized to spread and ransomware infection to other systems. This can be done through credential harvesting; multiple ransomware strains utilize programs such as Mimikatz libraries to pull the credentials from within memory and then pivot internally to other systems the harvested credentials have access to.
Storage Protection
Available as an additional add-on, Storage Protection can plugin through the ICAP protocol and can scan files as they are read / written to a NAS platform from within the enterprise environment. This can be utilized to target ransomware as it attempts to replicate itself onto shared drives and additional storage locations.
Policy Configuration
There are also multiple policy configuration adjustments that can be made to increase Ransomware prevention. Bitdefender's Hyper Detect technology which is utilized to detect advanced attacks and suspicious activities pre-execution can be set to Aggressive for Ransomware and Exploits. Ransomware vaccine can be enabled under the On-Access section to enable the “flags” that ransomware leaves behind to not infect a system that is currently infected. The Sandbox analyzer can be enabled for Applications, Scripts, Emails, Archives, and Documents so that previously unknown files can be detonated in a controlled environment and retroactively remediated as discussed previously in this article. Network Protection can be enabled to block specific categories of sites, perform endpoint level SSL decryption to inspect sites that may cause the infection, and the Anti-Phishing module can be enabled to prevent credential theft which can be utilized as an attack vector for malicious actors to gain a foothold in the environment to release ransomware.
Closing
While it is always important to select a competitive endpoint protection product, it is also very important to follow proper IT hygiene. Restricting end user permissions, network micro segmentation, and user access controls could have prevented the threat as the ransomware infection would not have been able to encrypt additional files or locations. With Bitdefender's multiple detection and response layers, organizations can remain safe and catch the threat earlier in the attack chain.
Citations
“PROTECT YOUR ORGANIZATION AGAINST RANSOMWARE” Bitdefender, 2020, https://www.bitdefender.com/business/cyber-threats-solutions/anti-ransomware.html.


.png)
.png)